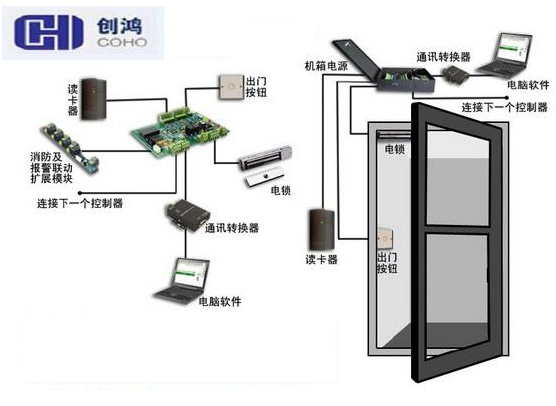
Analysis of the Design and Implementation of Networked Security Attendance and Access Control System Based on Mobile Phone
The access control system is one of the high-tech safety facilities that has been widely used in China in recent years and has become one of the intelligent signs of modern architecture. Today, with more and more emphasis on business intelligence and security, the access control system is given to the staff of the control centers and civil aviation airports of some important institutions, research laboratories, archives, and public utilities that are related to the national economy and the people's livelihood. These have further expanded and enhanced the role and function of the access control system. With the deepening of the electronic intelligence of the society, different types of access control and attendance systems have appeared on the market: password access control system, card access control system, and biometric access control system. Password access control system: By entering the password, the system determines that the password is correct and drives the electric lock, and opens the door to release. Its advantages: just remember the password, no need to carry other media. The lowest cost. Disadvantages: Slow speed, it usually takes several seconds to enter the password. If there are too many people entering and leaving, you need to queue. If you make a mistake, you will need to re-enter it and it will take longer. Poor security, people next to it are easy to remember someone else's password by gesture, the password is easy to forget or leak. Swipe access control system: According to the type of card, it is divided into contact card access control system (magnetic strip card barcode card) and contactless card (also called proximity card RF card) access control system. The card access control system is easy to wear due to contact, the number of uses is small, the card is easily damaged, and the scope of use has become less and less. Non-contact IC card, because of its durability, cost-effective, fast reading speed and high security, is the mainstream of the current access control system. However, personnel need to carry a dedicated IC card with them, otherwise they will not be able to enter and exit, which also brings some inconvenience to the modern fast-paced life. Biometric access control system: An access control system that identifies an identity based on the biological characteristics of the human body. Common are: fingerprint access control system (various fingerprint characteristics of each person), palm type access control system (different bone shape of each person's palm) iris access control system (each person's retina through optical scanning is different ) Portrait recognition access control system (each person's features and location are different) and so on. The advantage of the biometric access control system is that it does not need to carry a medium such as a card, and the probability of repetition is small, it is not easy to be copied, and the security is high. The disadvantage is: high cost. Because biometric identification needs to compare many parameter features, the comparison speed is slow, which is not conducive to the occasion of too many people. The biological characteristics of the human body change with the environment and time, so it is easy to produce a rejection rate (it is obviously this person, but his biological characteristics have changed, and he is not considered to be himself), for example, fingerprints are different due to season and dry humidity. Unlike the palm shape and portrait, the iris changes due to age, and the iris changes due to eye disease. Therefore, although the biometric access control system is advanced and safe, due to its high cost and limited application range, it is not the mainstream of the current access control system. Due to the various defects of the above various attendance systems, the use of the above-mentioned attendance technology will bring a lot of inconvenience to the user. Now that Wi-Fi-enabled mobile phones are becoming more and more popular, it is more convenient to use Wi-Fi-enabled mobile phones for personnel access registration management in companies or communities. Users don't need any extra equipment, just need a Wi-Fi-enabled mobile phone, which is not only easy to use, but also greatly reduces the deployment cost of the entire system. The MAC address of the Wi-Fi module in the mobile phone is unique, so it can be used in the attendance system to realize the identification of the person's identity without using other special equipment. In addition, when the attendance machine is connected to the remote server, if there is no corresponding security measure, it is vulnerable to attack and transmit error and disguised information. Based on the PIC32 Ethernet Starter KIT, this project expands the embedded Wi-Fi module to obtain the identity authentication information sent by the mobile phone Wi-Fi, and uses the AES security algorithm for encryption to realize a simple, secure and reliable networked identity authentication access control system. . A wireless LAN WLAN is a network of two or more computers connected by a wireless device. Originally originated from the ALOHA network of the University of Hawaii in 1970, it is a two-way star topology in which the entire system is wirelessly connected to a central computer via seven computers distributed over four islands. The first version was released in 1997, and two additional versions of 802.11a/b were added in 1999. The industry then established the Wi-Fi Alliance to address production and device compatibility issues for 802.11 compliant products. Wireless LAN has the following characteristics: ♦ Easy to use: Since there are no cable restrictions, users can access these resources in convenient places near network resources, such as homes, offices and other places. ♦ Mobility: As more and more places open wireless networks, users can even access the Internet outside the workplace. For example, a coffee shop or other places can easily access the Internet through a wireless network. ♦ Flexible deployment: Compared to wired networks, wireless networks do not require wiring and are therefore not affected by the surrounding environment. ♦ Good scalability: On the basis of the original network, the network can be expanded by adding an AP. In addition to the addition of switches and other devices, the wired network requires additional wiring, which not only increases the cost but also has poor flexibility. ♦ Security: Use a shared key encryption mechanism WEP (Wired Equivalent Privacy), WPA, WPA2 (Wi-Fi) network security access and other encryption mechanisms. The types of wireless LAN networks are: Ad-hoc, bridged, and distributed. ♦ Point-to-point: A point-to-point network allows wireless devices to communicate directly with each other. Wireless devices within the communication range can be discovered each other and can communicate directly without the AP. This type of communication is widely used in two computers, and they do not need to communicate over the network. The ad-hoc network is such a network. ♦ Bridging: Bridges connect different types of networks, wireless Ethernet bridges can connect to wired Ethernet and wireless networks, and bridges act as connection points for wireless LANs. ♦ Wireless distributed system: When it is difficult to connect all access points in a network through a cable, you can use the AP as a repeater.
The composite terminal is a typical representative of the connector (CONNECTOR), which is composed of a plug (female) and a socket (male) to realize the connection function. For the transfer of voltage, current and signal, this series is characterized by safe, reliable and stable contact, and is mainly used in electric power, communication, industrial control and other industries.
composite terminal block,component terminal block,composite terminal block adapter Sichuan Xinlian electronic science and technology Company , https://www.sztmlchs.com