Multi-level, pre-integrated protection against IoT zombie attacks
The Internet of Things zombies are coming. They are numerous and we cannot destroy them all in the short term. They are likely to jeopardize the safety of your equipment. Therefore, measures should be taken now to ensure that your equipment is protected from infection. In the previous blog post (IoT zombies devour the Internet), we delved into the recent large-scale DDoS (Distributed Denial of Service) attacks. In these attacks, IoT devices are used as robots or zombies. Shortly after the blog post was published, a person claiming to be the author of the malware published the source code of the attack software. The malware called Mirai is a Trojan virus. After infecting Internet of Things devices, it launched a DDoS attack on a number of well-known websites. The number of victim devices is staggering. Malware Tech estimates that 120,000 devices are infected, while Level 3 claims that 1.5 million devices are infected. This attack is only the latest example. These viruses are permanent. When thinking about how to deal with attacks, it is very helpful for us to borrow a medical virology to better understand how Mirai is spread. The medical infection analysis method uses a graph to express the relationship between infection, infection, and repair. This method also applies to the problems we are facing now: Once the device is infected, it uses a pseudo-certificate to look for devices with open Telnet ports on the network. Once such a device is found, the Trojan virus is implanted into it, turning it into the same opportunity to infect more targets. This process is shown in the first paragraph of the graph above. Some devices can be repaired or protected, but many can't, so they become permanently infected devices. Even those devices that have been repaired cannot be reinfected by other infected devices. As many devices are permanently infected, attacks can come back at any time. Can we kill the Mirai virus? There are ways to kill the Mirai virus, or at least limit its effects. Repair all devices In fact, this is impossible. Most device owners don't know that their devices are infected, they don't have the skills to repair them, and they don't even want to fix them (because they are not directly affected). Block control - command server One of Mirai's weaknesses is that newly infected devices need to be registered with the command-control server before downloading instructions. These are the servers that spread the virus, not the potentially infected devices. If the Control-Instruction Server is blocked, it will limit the spread of the Mirai virus. Protection target In response to the recent Internet of Things DDoS attacks, the security website krebsonsecurity.com was forced to replace the hosting company. DDoS attacks are not new, defenses are still there, and such transfers are one of the effective countermeasures. However, in the end, it is not realistic to fix all the devices that are currently infected or potentially infected, and we can't completely clean up the infection. Prospect Even if it is not Mirai, other self-propagating malware will be developed to infect other IoT devices. The disclosure of the Mirai source code will speed up the development of subsequent viruses. The disclosure of the Mirai source code will cause this code to be widely used and developed. It is foreseeable that future attacks will remove the reliance on the command and control servers, making the anti-virus task even more difficult. Currently, Mirai mainly conducts DDoS attacks. But in the future, it will use IoT devices as zombie IoT devices to attack other systems on the same network. Device immunity It seems that IoT zombies will exist for the foreseeable future. We can avoid even quarantining IoT zombies, but as the network changes and new devices evolve, new viral infections will follow. Since the risk of infection persists, it is only a matter of time before the device becomes an infection target. Therefore, it is important to immunize the device to protect it from infection. Clearly, the first step in immunization is first to eliminate known infection patterns. Eliminate or block unnecessary services (such as Telnet), eliminate the default certificate, replace it with a secure password, and block accidental connections to external endpoints. But in the long run, further steps are needed to prevent vulnerabilities that can be exploited by adaptive viruses. This is the role of tools such as CWE/SANS Top 25 Most Dangerous Software Errors (), and it is also where Wind River can work. Wind River products can provide the following multi-level, pre-integrated protection measures: - Secure boot and initialization to protect against affected executable code - Static data encryption, protection of certificates and other sensitive information - Two-way authentication to block illegal terminals and malicious attempts to connect - Communication encryption to protect sensitive information - Operating system enhancements to prevent privilege escalation - Firewall blocks unexpected external access or unexpected external connections - Security update modifications require authorization to prevent malicious modifications
This series high power density programmable DC electronic load provides three voltage ranges 200V DC Electronic Load/600V DC Electronic Load /1200V DC Electronic Load. Supports CV, CC, CR and CP these 4 basic operating modes, as well as CV+CC, CV+CR, CR+CC these 3 complex operating modes. Full protection includings OCP, OPP, OTP, over voltage and reverse alarm. Support external control and monitor mode, the 0 to 10V input or output signal represent 0 to full range voltage or current. Provide OCP test, OPP test and Short circuit simulation to effectively solve the application demands for power and automated testing. Built-in RS232, RS485 and USB communication interfaces, LAN&GPIB communication card is optional. Two or more loads can be connected in master-slave parallel mode to provide more power or current capacity,which can make DC Electronic Load System in 200V DC Electronic Load System,600V DC Electronic Load System,1200V DC Electronic Load System . This series DC load can be applied to battery discharge, DC charging station and power electronics and other electronics products.
Speical features as below:
â— Flippable front panel and color touch screen allow convenient access and operation DC electronic load,electronic load,DC load,ac electronic load, electronic load APM Technologies Ltd , https://www.apmpowersupply.com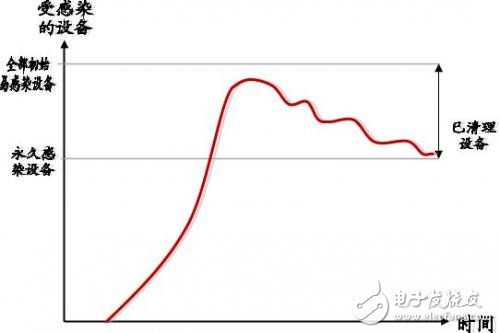
â— Provides four kinds of basic working mode such as CV/CC/CR/CP, and CV+CC/CV+CR/CR+CC complex operating modes
â— Adjustable current slew rate, adjustable CV loop speed
â— Ultra high precision voltage & current measurement
â— OCP/OPP testing function
â— 50kHz high-speed CC/CR dynamic mode
â— 500kHz high-speed voltage and current sampling rate
â— Timing & discharging measurement for batteries
â— Short circuit test mode
â— Auto mode function provides an easy way to do complicated test
â— Dynamic frequency sweep function for determining worst case voltage peaks*
â— Non linear load mode function makes the simulated loading current more realistic*
â— Supports external analog control function*
â— V-monitor/I-monitor
â— LED load simulation function
â— Full protection: OCP, OPP, OTP, over voltage and reverse alarm
â— Up to 20 units master/slave parallel control
â— Front panel USB interface supports data import and export
â— SCPI language and standard rack size make it ideal for ATE System integration
â— Smart fan control with lower noise and better for environment
â— Multi versions to meet the cost performance and different applications
* Only professional Electronic Load units support these functions